Glossary of Scam Terms












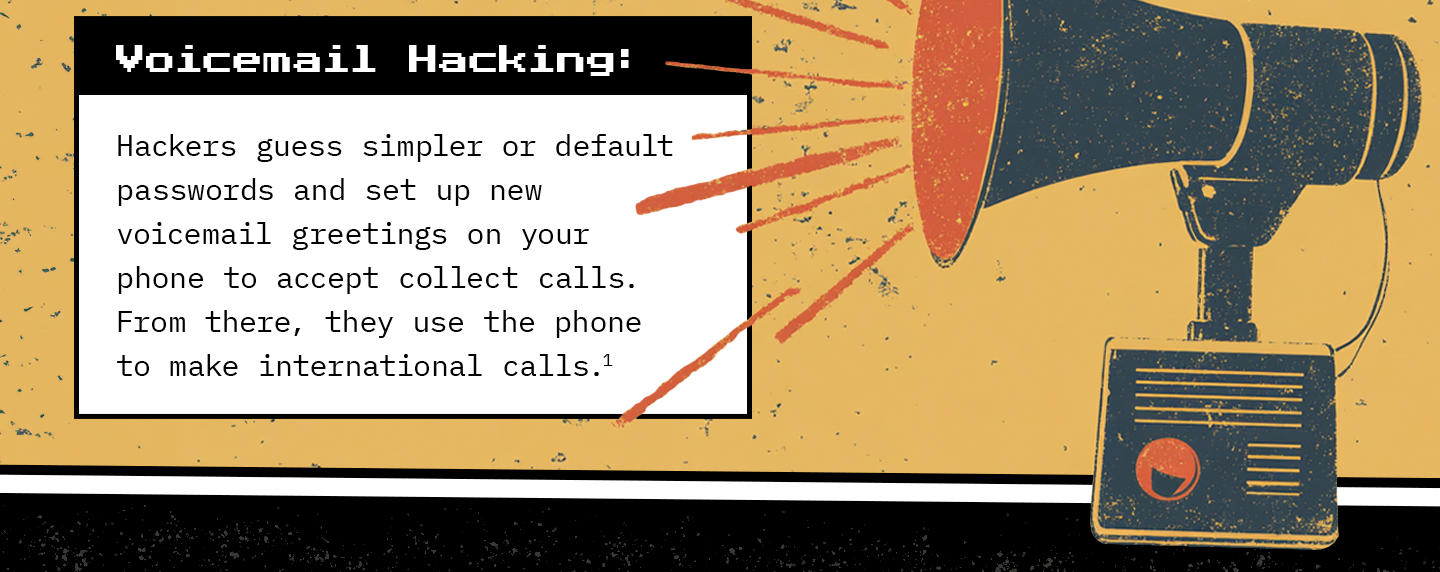






















Do you know how to set up your financial goals for success? This knight does.

There are numerous ways to supplement your Medicare insurance coverage. This article helps you explore your options.

If you’re thinking of leasing a new car, then you shouldn’t forget about gap insurance.